
Computers communicate using networks. These networks could be on a local area network LAN or exposed to the internet. Network Sniffers are programs that capture low-level package data that is transmitted over a network. An attacker can analyze this information to discover valuable information such as user ids and passwords.
In this article, we will introduce you to common network sniffing techniques and tools used to sniff networks. We will also look at countermeasures that you can put in place to protect sensitive information been transmitted over a network.
Topics covered in this tutorial
What is network sniffing?
Computers communicate by broadcasting messages on a network using IP addresses. Once a message has been sent on a network, the recipient computer with the matching IP address responds with its MAC address.
All present and past releases can be found in our download area. Installation Notes. For a complete list of system requirements and supported platforms, please consult the User's Guide. Information about each release can be found in the release notes. Each Windows package comes with the latest stable release of Npcap, which is required for live packet capture. Wifi sniffer free download - WiFi Scanner, Easy WiFi, Hotspot Shield, and many more programs. Enter to Search. My Profile Logout. CNET News Best Apps. Download Wifi Sniffer Mac Software. AirGrab WiFi Radar v.1.7.39 AirGrab WiFi Radar is a tool to display information about Apple Airport base stations and other WiFi wireless access points. Using AirGrab WiFi Radar you can determine most popular WiFi channels and select optimal channel for your.
Kismet Kismet is a wireless network and device detector, sniffer, wardriving tool, and WIDS (wireless intrusion detection) framework. Kismet works with Wi-Fi interfaces, Bluetooth interfaces, some SDR (software defined radio) hardware like the RTLSDR, and other specialized capture hardware. WiFi Analyzer can help you to identify Wi-Fi problems, find the best channel or the best place for your router/access-point by turning your PC/laptop, tablet or mobile device into an analyzer for your wireless network. The basic version is completely ad-free and additional.
Network sniffing is the process of intercepting data packets sent over a network.This can be done by the specialized software program or hardware equipment. Sniffing can be used to;
- Capture sensitive data such as login credentials
- Eavesdrop on chat messages
- Capture files have been transmitted over a network
The following are protocols that are vulnerable to sniffing
- Telnet
- Rlogin
- HTTP
- SMTP
- NNTP
- POP
- FTP
- IMAP
The above protocols are vulnerable if login details are sent in plain text
Passive and Active Sniffing
Before we look at passive and active sniffing, let’s look at two major devices used to network computers; hubs and switches.
A hub works by sending broadcast messages to all output ports on it except the one that has sent the broadcast. The recipient computer responds to the broadcast message if the IP address matches. This means when using a hub, all the computers on a network can see the broadcast message. It operates at the physical layer (layer 1) of the OSI Model.
The diagram below illustrates how the hub works.
A switch works differently; it maps IP/MAC addresses to physical ports on it. Broadcast messages are sent to the physical ports that match the IP/MAC address configurations for the recipient computer. This means broadcast messages are only seen by the recipient computer. Switches operate at the data link layer (layer 2) and network layer (layer 3).
The diagram below illustrates how the switch works.
Passive sniffing is intercepting packages transmitted over a network that uses a hub. It is called passive sniffing because it is difficult to detect. It is also easy to perform as the hub sends broadcast messages to all the computers on the network.
Active sniffing is intercepting packages transmitted over a network that uses a switch. There are two main methods used to sniff switch linked networks, ARP Poisoning, and MAC flooding.
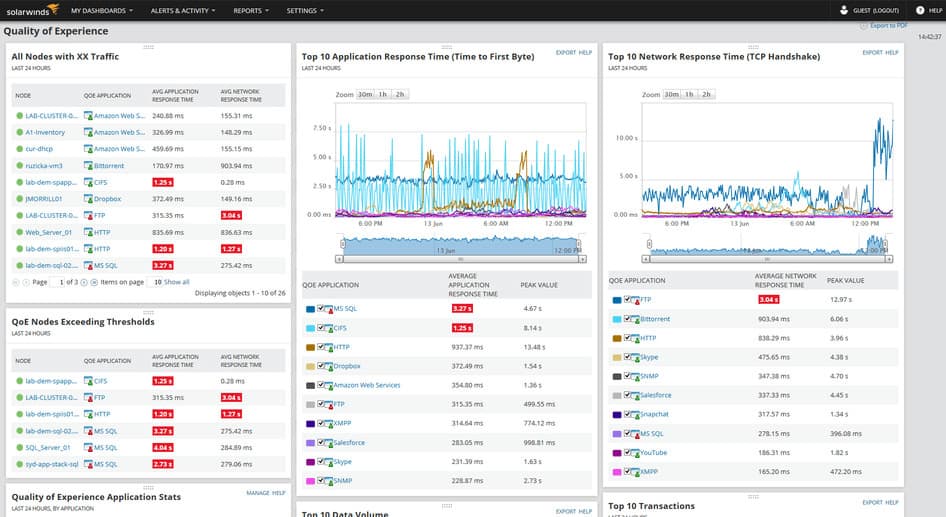
Hacking Activity: Sniff network traffic
In this practical scenario, we are going to use Wireshark to sniff data packets as they are transmitted over HTTP protocol. For this example, we will sniff the network using Wireshark, then login to a web application that does not use secure communication. We will login to a web application on http://www.techpanda.org/
The login address is This email address is being protected from spambots. You need JavaScript enabled to view it., and the password is Password2010.
Note: we will login to the web app for demonstration purposes only. The technique can also sniff data packets from other computers that are on the same network as the one that you are using to sniff. The sniffing is not only limited to techpanda.org, but also sniffs all HTTP and other protocols data packets.
Sniffing the network using Wireshark
The illustration below shows you the steps that you will carry out to complete this exercise without confusion
Download Wireshark from this link http://www.wireshark.org/download.html
- Open Wireshark
- You will get the following screen
- Select the network interface you want to sniff. Note for this demonstration, we are using a wireless network connection. If you are on a local area network, then you should select the local area network interface.
- Click on start button as shown above
- Open your web browser and type in http://www.techpanda.org/
- The login email is This email address is being protected from spambots. You need JavaScript enabled to view it. and the password is Password2010
- Click on submit button
- A successful logon should give you the following dashboard
- Go back to Wireshark and stop the live capture
- Filter for HTTP protocol results only using the filter textbox
- Locate the Info column and look for entries with the HTTP verb POST and click on it
- Just below the log entries, there is a panel with a summary of captured data. Look for the summary that says Line-based text data: application/x-www-form-urlencoded
- You should be able to view the plaintext values of all the POST variables submitted to the server via HTTP protocol.
What is a MAC Flooding?
MAC flooding is a network sniffing technique that floods the switch MAC table with fake MAC addresses. This leads to overloading the switch memory and makes it act as a hub. Once the switch has been compromised, it sends the broadcast messages to all computers on a network. This makes it possible to sniff data packets as they sent on the network.
Counter Measures against MAC flooding
- Some switches have the port security feature. This feature can be used to limit the number of MAC addresses on the ports. It can also be used to maintain a secure MAC address table in addition to the one provided by the switch.
- Authentication, Authorization and Accounting servers can be used to filter discovered MAC addresses.
Sniffing Counter Measures
- Restriction to network physical media highly reduces the chances of a network sniffer been installed
- Encrypting messages as they are transmitted over the network greatly reduces their value as they are difficult to decrypt.
- Changing the network to a Secure Shell (SSH)network also reduces the chances of the network been sniffed.
Summary
Sniffer Wifi Mac Os X
- Network sniffing is intercepting packages as they are transmitted over the network
- Passive sniffing is done on a network that uses a hub. It is difficult to detect.
- Active sniffing is done on a network that uses a switch. It is easy to detect.
- MAC flooding works by flooding the MAC table address list with fake MAC addresses. This makes the switch to operate like a HUB
- Security measures as outlined above can help protect the network against sniffing.
In this series of blogposts we will cover advanced, security focused, aspects of the ESP8266 /ESP32 SoCs such as sniffing and injecting 802.11 and bluetooth packets, building proof-of-concept network implant devices, etc.
The ESP8266 is a low-cost Wi-Fi capable system-on-chip with full TCP/IP stack produced by Espressif Systems. It features a Tensilica L106 32-bit RISC processor, reaching a maximum clock speed of 160 MHz.
It integrates several peripheral interfaces via its 17 GPIO (General Purpose I/O) ports, which can be assigned to various functions, such as:
- Hardware and Software SPI interface
- I2C Interface
- I2S Interface
- Universal Asynchronous Receiver Transmitter (UART)
- Pulse-Width Modulation (PWM)
- IR Remote Control
- 10 bit resolution ADC (Analog-to-Digital Converter)
Sniffer interface
The ESP8266 SDK API features a promiscuous mode which can be used to capture IEEE 802.11 packets in the air, with some limitations though. It will only decode 802.11b/g/n HT20 packets (20Mhz channel bandwidth), not supporting HT40 packets or LDPC. For those, it will only return their length and other (scarce) low-level information, but no additional decoding will be performed.
Data structures
Several data structures are used (but not exposed, i.e. they need to be explicitly declared in the user program) by the SDK to represent these two kinds of packets:
Sniffer-related API functions
Free Network Sniffer
The ESP8266 SDK provides the following sniffing-related functions, which can be found at /include/user_interface.h:
void wifi_promiscuous_enable(uint8 promiscuous)
Enables the promiscuous mode; to do so the chip must be both in Station mode first and disconnected from any AP.
The uint8 promiscuous parameter enables (1) and disables(0) this mode.
void wifi_set_promiscuous_rx_cb(wifi_promiscuous_cb_t cb)
Registers the callback function which will be called when a data packet is received.
The callback function will get two parameters: a pointer to the buffer memory containing the received packet and its length. The latter determines the type of the received packet:
- Management packets. Length will be
sizeof(wifi_pkt_mgmt_t). The buffer will hold awifi_pkt_mgmt_tstructure, containing:wifi_pkt_rx_ctrl_tstructure- A buffer containing the 802.11 packet
cntwill be1lenwill be the length of the buffer
- Data packets. The buffer will hold a
wifi_pkt_data_tstructure, containing:wifi_pkt_rx_ctrl_tstructurebufcontains the 802.11 headercnthow many packets are inbuflenseqcontains one or morestruct LenSeq, providing the following data:- total packet length
- both source and destination MAC addresses
- Unsupported packets. Length will be
sizeof(wifi_pkt_rx_ctrl_t). Either the received packet is not supported or it was badly formed/received.
void wifi_promiscuous_set_mac(const uint8_t *address)
Sets a destination MAC address filter for the sniffer, which will filter out every packet except those addressed to the specified MAC or to the broadcast (FF:FF:FF:FF:FF:FF).
Sample:
uint8 wifi_get_channel(void)
Returns the current Wi-Fi channel.
Writing a simple packet sniffer
Environment setup
Full code is available on GitHub as a PlatformIO project.
It was tested on a Adafruit HUZZAH feather board, with the Arduino framework, using ESP8266 SDK version 1.3.0.
IEEE802.11

A standard 802.11 frame contains a layer 2 MAC header, followed by a variable length frame body and a 32 bit checksum (FCS):
There are several different types of packets:
- Management
- Control
- Data
- Misc
Our simple sniffer will parse and print out the information contained in the frame header; additionally it will extract the SSID from beacon frames:
Program flow

By calling wifi_set_promiscuous_rx_cb() we can specify the callback function that will be called when the network interface receives a new packet.
The overall program flow will be:
- Initialisation
- Initialise serial interface
- Enable promiscuous mode
- Set sniffer callback
- Set wifi channel (or implement channel hopping via hardware timers)
- Print output table header
- Main loop
- Does nothing: just waits for the callback to be triggered
- Callback function
- Initialise pointers to data structures within the raw packet
- Extract and parse the information contained in the different fields
- Format and output
Due to the blocking nature of the callback function, it is not a good idea to perform too much process in it, because we might lose packets in the meantime. However, this simple example is focused on demonstrating the SDK calls usage rather than in efficiency.
Sniffer Wifi For Mac Os
The initialisation phase will be implemented on the setup() function:
Our callback function will then parse each raw packet (buff) as follows:
Data structures
In order to parse the packets the following data structures were used: